What Is the MITRE ATT&CK Framework?
The MITRE ATT&CK® framework is a globally recognized knowledge base of tactics and techniques used in cyberattacks. ATT&CK is an acronym for Adversarial Tactics, Techniques, & Common Knowledge. This comprehensive framework is free and preferred by threat hunters, red teamers, and other technical security roles as it helps them map the lifecycle of an attack.
The Benefits of the MITRE ATT&CK Framework
As attacks became more complex there was a need for standard taxonomy and language for professionals to communicate and defend. Categorizing tactics, techniques, and procedures of the adversaries provides several benefits, including:
How Is the Framework Organized?
The MITRE ATT&CK knowledge base is organized into a comprehensive matrix. There are three matrices, but one most often used is Enterprise ATT&CK, which focuses on Windows, macOS, Linux, Cloud, and others common IT platforms. The Enterprise ATT&CK matrix consists of 14 tactics, each containing a set of techniques and sub-techniques with more being added regularly.
Use Cases for the MITRE ATT&CK Matrix
There are several ways security teams can use the matrix.
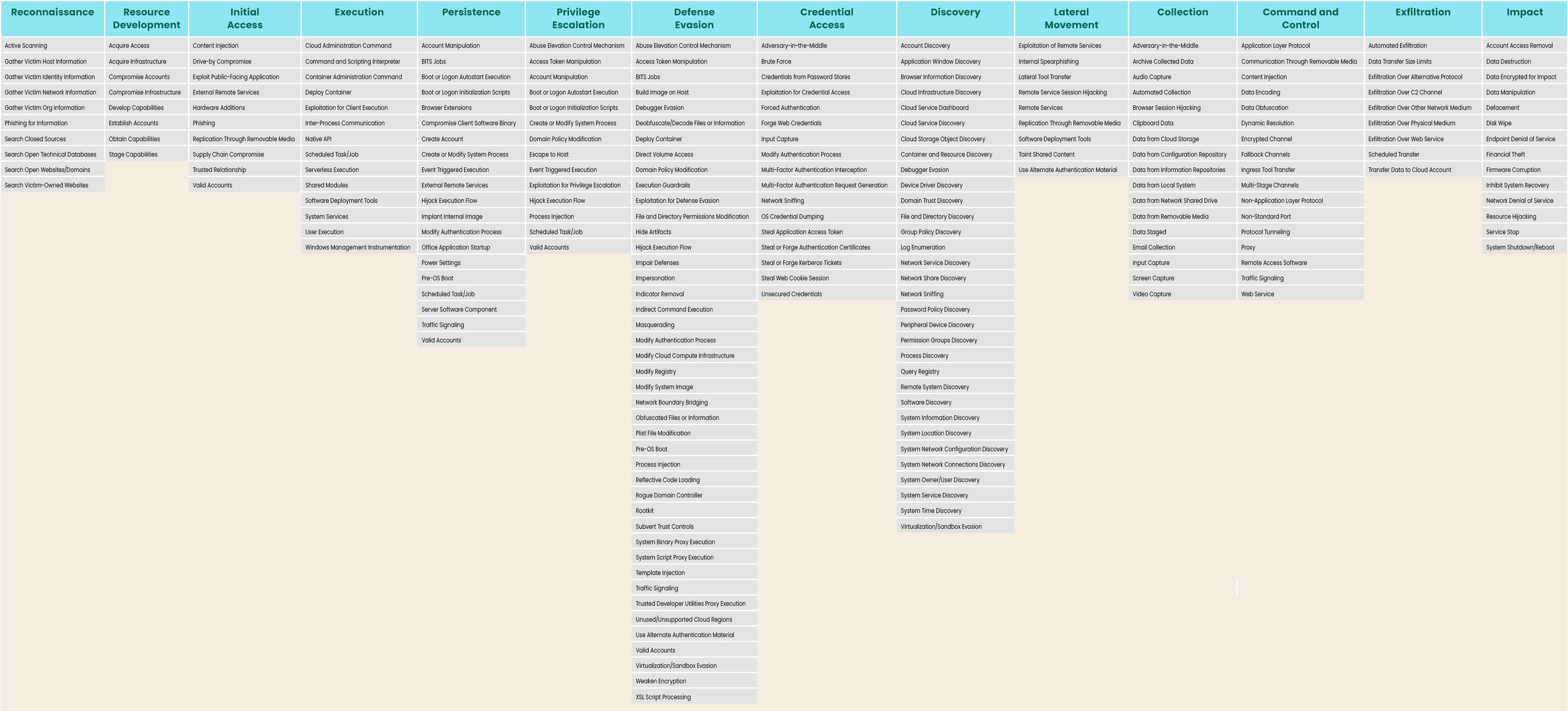
The MITRE ATT&CK Matrix
The MITRE ATT&CK Matrix shows attack tactics on the top row. Each column represents the techniques for each tactic.
Fortra and the MITRE ATT&CK Framework
Fortra security solutions help organizations across the entire framework. Below are each of the controls along with the solutions that can help address them.
Our team is ready to answer your questions.
Our team of expert problem solvers is ready to find answers to your organization’s toughest problems.