Prevent IBM i Security Breaches
Protect your organization from the high cost of security breaches by tracking and monitoring data access with Powertech Exit Point Manager for IBM i software. An easy-to-use interface enables administrators to better follow security policy, resulting in a network that’s more secure, more likely to be compliant with regulatory requirements, and less vulnerable to threats.
Control Exit Points
Secure network access points that traditional menu security plans don’t protect. Safeguard your IBM i systems by closing any and all back doors to the network, including FTP, ODBC, SQL, JDBC, and Remote Command. Monitoring and controlling exit point traffic helps restrict data access only to authorized users.
Limit Access to Sensitive IBM i Data
Limit access to specific objects and libraries to only the users and groups who have a demonstrated business need. Assign rules by IP address, allowing system access to be limited to approved locations. Easily change and apply rules across your network, with Powertech Exit Point Manager for IBM i.
Maintain an Audit Trail
Monitor and track users who access data and issue remote commands. Satisfy regulatory initiatives by recording transactions to a secure journal.
[Powertech Exit Point Manager for IBM i] is an intuitive exit point control software that allows us to really lock down our network and improve our IBM i compliance.
Emily Shellabarger, Vice President of First Security Bank, First Security Bank
Key Features
System access monitoring
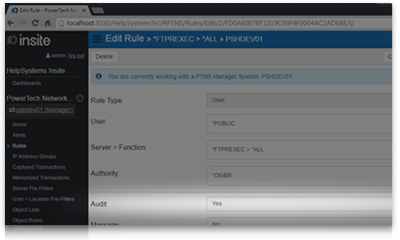
Track, monitor, and control access to system data. Record user activity, such as who is accessing data and issuing remote commands, in a secure journal. Print reports or analyze data with Microsoft Excel or other tools to more efficiently assess your network security.
Access rule implementation
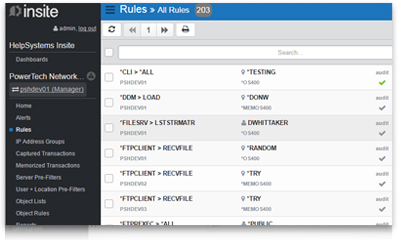
Dynamic rule configuration helps you comply with your security policy. Powertech Exit Point Manager for IBM i allows you to grant access only to users or groups who need it, restrict access to specific objects and libraries, and allow access for only locations approved by policy. Powertech Exit Point Manager for IBM i allows multiple levels of access control, giving you the flexibility to meet your specific requirements.
Exit point control
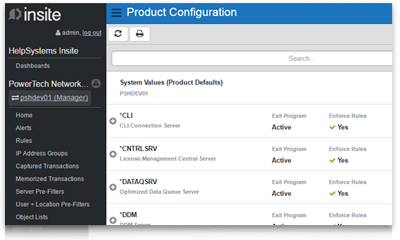
Control access to your IBM i by monitoring and restricting exit point traffic. With Powertech Exit Point Manager for IBM i, you can limit data access to only users who are authorized to download or upload it.
Event notification
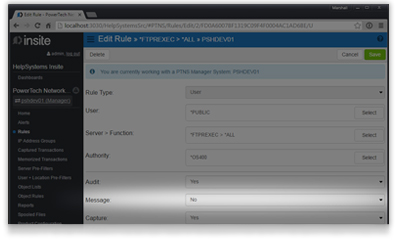
Network transactions may indicate that critical data is at risk. When these events occur, Network Security will send messages to network administrators in real time, helping you address security concerns before data is compromised.
Intuitive browser interface
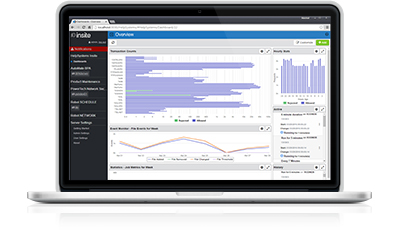
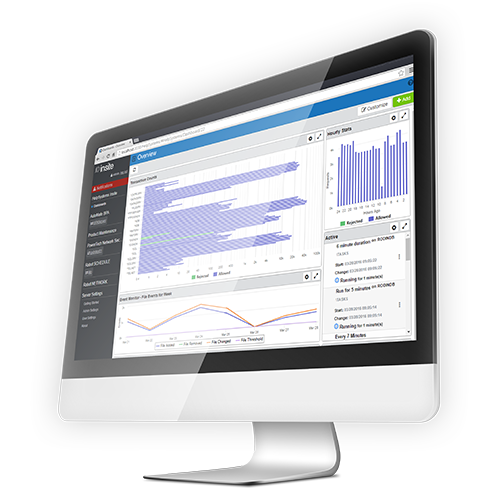
Get greater visibility to key performance indicators with Insite. Dashboards display transaction values without running reports, so you never risk missing issues because you didn’t have time to create a report. Enhanced filtering and search functionality helps you find the information you need quickly. Plus, the mobile-friendly interface provides easy navigation on any device.
Centralized security administration
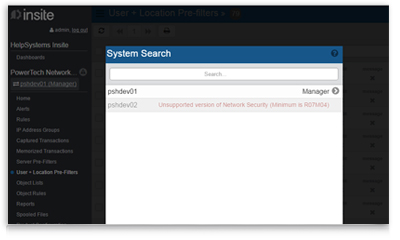
Configure rules and settings just once on the management system. Copy them to other endpoints, quickly propagating your security policy across your network. User-friendly dashboards show you at a glance what’s happening across your network.
Active analytics
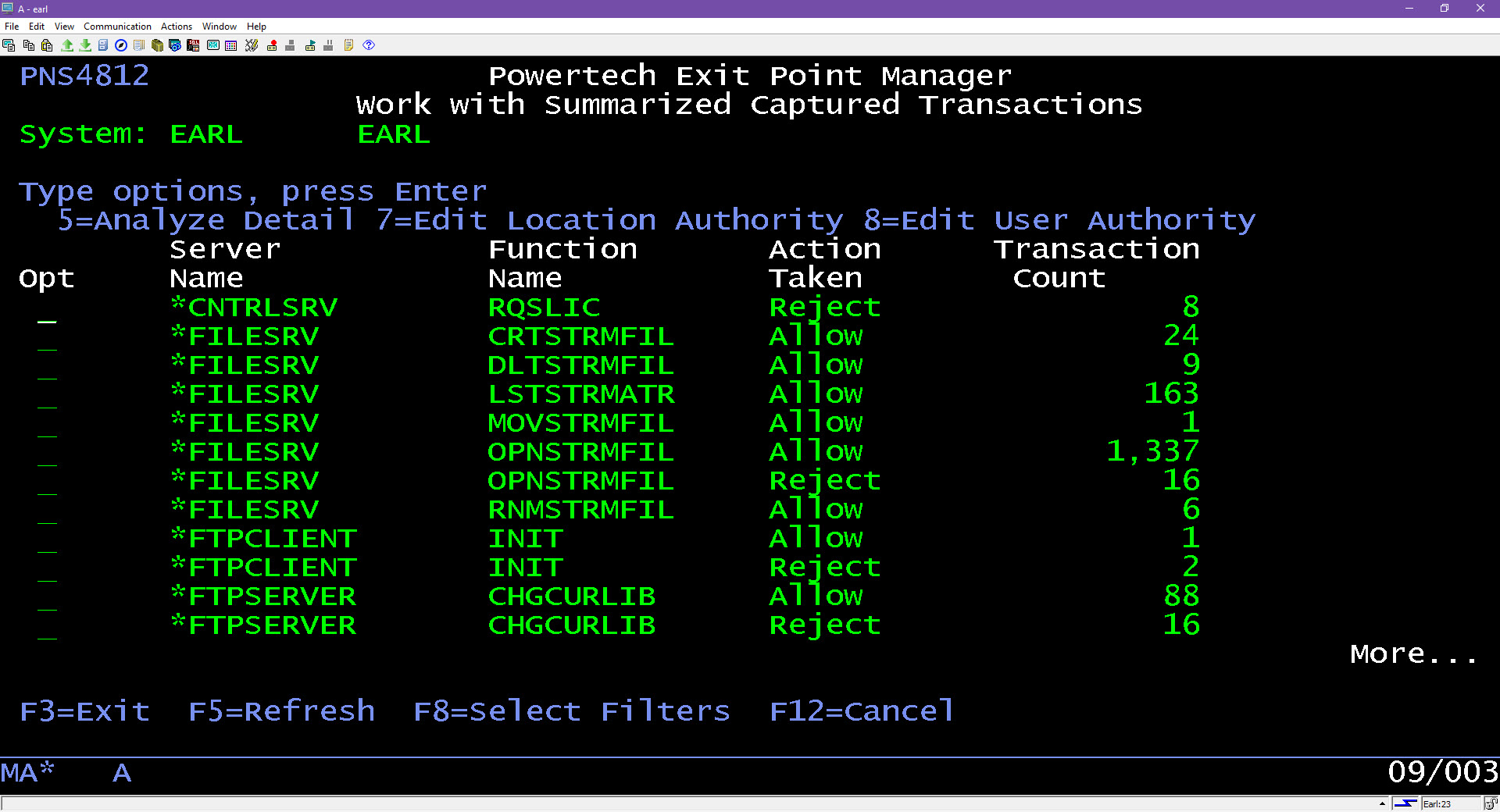
Exit Point Manager’s active analytics feature provides real-time information regarding which users were allowed or blocked from accessing the system at various exit points. Data rolls up into hourly, daily, or monthly summaries, depending on your preference.
From there, you can traverse that data by starting at the top summary level and drilling down into the details. Users can pre-configure display filters, create new filters, use more detailed selection and sorting criteria, and maintain user views for future sessions.
Exit Point Manager for IBM i Case Studies
Explore Exit Point Manager for IBM i Resources
Available Services for Powertech Exit Point Manager for IBM i
Consulting
When you’re short on time or expertise, our consultants help get you up and running to make sure your project is done right.
Powertech Exit Point Manager reduces the risk of unauthorized and unaudited server access by regulating user access to data and commands.
Get Started
Close back doors to your network, log exit point transactions, and enforce your security policy. See our Powertech Exit Point Manager for IBM i software in action in a demo.
Want to secure your IBM i?
In just 10 minutes, find out where your IBM i security currently stands with a free Fortra Security Scan. We’ll evaluate your system’s vulnerabilities and suggest steps you can take to protect your critical data. It’s quick and easy, with no obligation to you.
