The Fortra Security Scan is the place to start when you want to secure your IBM i (System i®, iSeries®, AS/400®). The free Scan provides a snapshot of your current system security in just 10 minutes. It runs directly from a network-attached PC, without modifying any system settings. The Security Scan audits common security metrics and displays the results in an easy-to-read, browser-based application. A Fortra Security Advisor helps you interpret the results, and you can print the findings for your records.
Takeaways from the Security Scan

Input on Mitigating the IBM i's Biggest Vulnerabilities
We’ll walk you through the most common vulnerabilities that exist on the IBM I – such as excessive users with administrative privileges and misconfigured QSECURITY levels. We’ll provide you with detail on where they exist, how attackers go about exploiting them, and your organization’s readiness to defend against them and how it can be improved.
We’ll walk you through the most common vulnerabilities that exist on the IBM I – such as excessive users with administrative privileges and misconfigured QSECURITY levels. We’ll provide you with detail on where they exist, how attackers go about exploiting them, and your organization’s readiness to defend against them and how it can be improved.
What Your Critical System Values Are Set to and Recommended Settings
The Security Scan will take an inventory of your critical system values and compare them to best practices benchmarks so that you can see which specific settings require remediation.
The Security Scan will take an inventory of your critical system values and compare them to best practices benchmarks so that you can see which specific settings require remediation.

A PDF Report Summarizing Your Results
Results from the Security Scan will be compiled into a PDF report that offers in-depth evaluation of your security posture in the seven areas of security, including: user authorities, public authority, network access, FTP access, system security, user security, and system auditing.
Results from the Security Scan will be compiled into a PDF report that offers in-depth evaluation of your security posture in the seven areas of security, including: user authorities, public authority, network access, FTP access, system security, user security, and system auditing.

Personalized Security Plan
One of our IBM i security experts will talk you through your results and provide you with an individualized plan regarding specific items that require remediation as well as which areas of security require attention and the best practices you should employ in addressing them.
One of our IBM i security experts will talk you through your results and provide you with an individualized plan regarding specific items that require remediation as well as which areas of security require attention and the best practices you should employ in addressing them.
The Security Scan Reviews Critical Areas of IBM i Security
Executive Summary
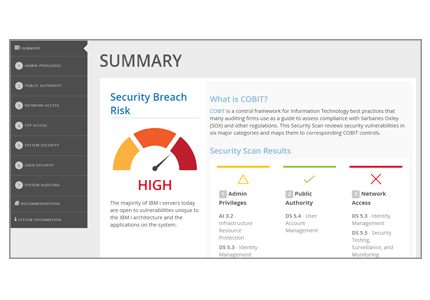
The Executive Summary ranks the overall condition of your system. Red, yellow, and green indicators compare your system against best practices, along with references to the COBIT framework to which they apply.
Administrative Rights
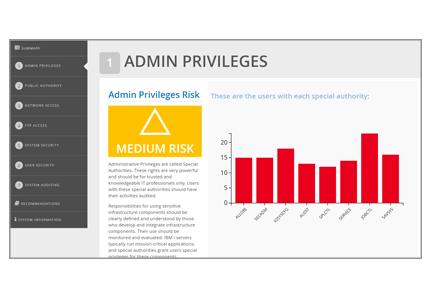
The Administrative Rights section reviews eight special authorities and the vulnerabilities of each.
Public Authority
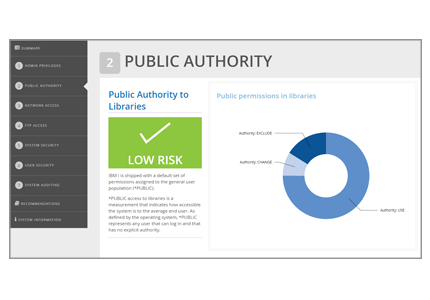
The public is any user with a profile and password, so this section indicates how accessible the system is to the average end user.
User Access to Data

The User Access section reviews user access to system data through common network access services, such as FTP, ODBC, and Remote Command.
FTP Access

The FTP Access section identifies security vulnerabilities caused by using FTP (file transfer protocol) to transfer files between a client and server on a network.
System Security

The System Security section examines key system values that control security settings on your system.
User Security
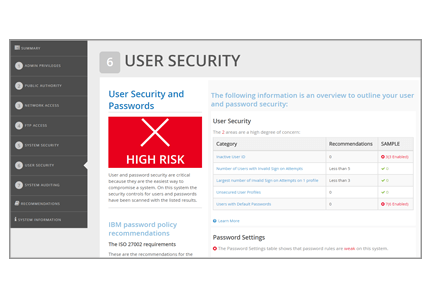
The User Security section reviews how many user profiles haven't been used for at least 30 days and how many have default passwords, as well as reviewing basic password settings.
System Auditing
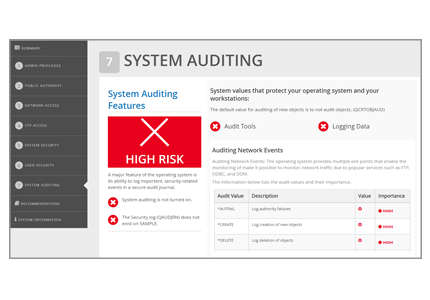
The System Auditing section checks if you are using the IBM i event auditing capabilities and the types of events being audited.
Recommendations

The Recommendations section provides suggestions for remediation based on the security checks performed on your system.
Why Should I Run a Security Scan?
The Security Scan examines your system’s vulnerabilities, and suggests steps you can take to protect your critical data.
A Security Scan is:
- Quick—The Scan runs in just 10 minutes
- Confidential—Only you see the results
- Thorough—A Security Advisor helps you understand the current state of your IBM i security
- Clear—You'll understand where your system is secure and the areas that need work
You’ll find out where your IBM i security currently stands, whether your system is at risk, and how to improve data protection.
View our FAQs >
Is Security Scan Safe?
Before requesting a Security Scan, you might wonder if the scan is safe—or if the Security Scan itself poses a risk to your data. The process is completely secure, and Fortra has performed thousands of scans for organizations around the world. To put your mind at ease, here are some more details about a Security Scan entails.
Security Scan leverages a proprietary, PC-based tool that was written by Fortra specifically for the purpose of this scan. We never request access to any network or server throughout this process and no application data is ever accessed. The program does not make any changes to any servers—except for the program’s installation and subsequent removal.
The Security Scan program runs in just one or two minutes, and it can be run on a production partition without any impact or interruption to business processes.
As a cybersecurity company, Fortra takes the safety and security of your systems very seriously. If you have any questions about how the Security Scan program works, contact us and we can provide more details.
What Do I Get after Running a Security Scan?

Results of your IBM i Security Scan are compiled immediately and presented for review in an easy-to-understand, browser-based, interactive reporting application. A Fortra Security Adviser can help you interpret the results, and you can save or print the findings for your records.
Security Scan does not leave files on your IBM i. The Security Scan application installs a licensed program to collect security data, but the files are removed upon completion of the analysis or you can remove the program manually using the DLTLICPGM command. You also have seven days after your Security Scan to make configuration changes and rerun the Scan to test your changes.