As a syslog server incessantly pings with every security notification, security teams can feel as though they are drowning in a sea of security warnings. Without a SIEM, it’s difficult to know which events are truly critical and which can be ignored. However, when a SIEM has been implemented, security teams get a much clearer picture of their environment’s security. There could truly be no threats, or multiple incidents may be occurring that simply have not yet affected performance.
But how exactly does a SIEM isolate the true threats from the general noise? This article seeks to illustrate the contrast between stagnant security events at an organization without a SIEM, and the distinct life cycle of events when a SIEM is streamlining security risks.
Threat Detection

Without a SIEM
A syslog server may constantly be churning out notifications, but the majority of hunting for potential threats is left to security teams.
With a SIEM
SIEMs are constantly processing event data and looking for threats from a variety of assets within an IT environment—networks, applications, devices, user activity logs, different operating systems, databases, firewalls, or network appliances.
Translation
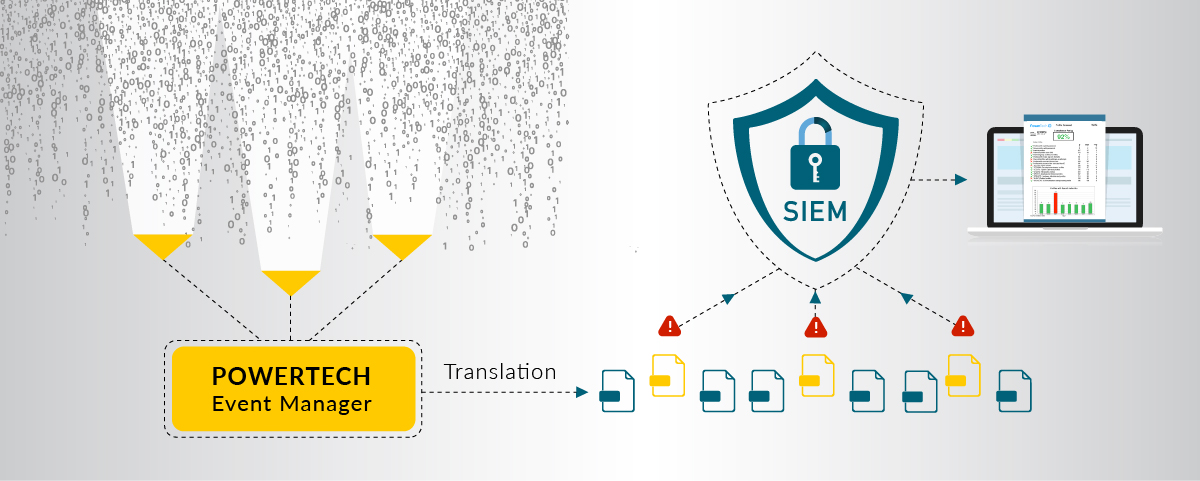
Without a SIEM
Custom configuration is needed to capture raw data of events that admins deem suspicious. This data can be in various formats, in distributed locations, with content that is relevant to each particular asset.
Translation and interpretation of this data is typically where a bottle neck occurs. It becomes virtually impossible to effectively sort through numerous logs and be knowledgeable about the various formats and messages produced by different sources. For example, if a database admin was reviewing multiple logs, it would be immensely difficult for them to discern or highlight activity in webserver logs that may be suspicious or need further review. This allows threats to progress much further before they are eventually caught.
With a SIEM
When a security event occurs, SIEMs like Powertech Event Manager immediately flag the event and capture all relevant raw data. This raw data is then translated into a common format, where the SIEM can then automatically interpret and classify how critical the risk is.
Prioritization
Without a SIEM
Classification is left to the security teams to assign, with no additional guidance on which events hold the biggest potential for harm to the IT environment.
With a SIEM
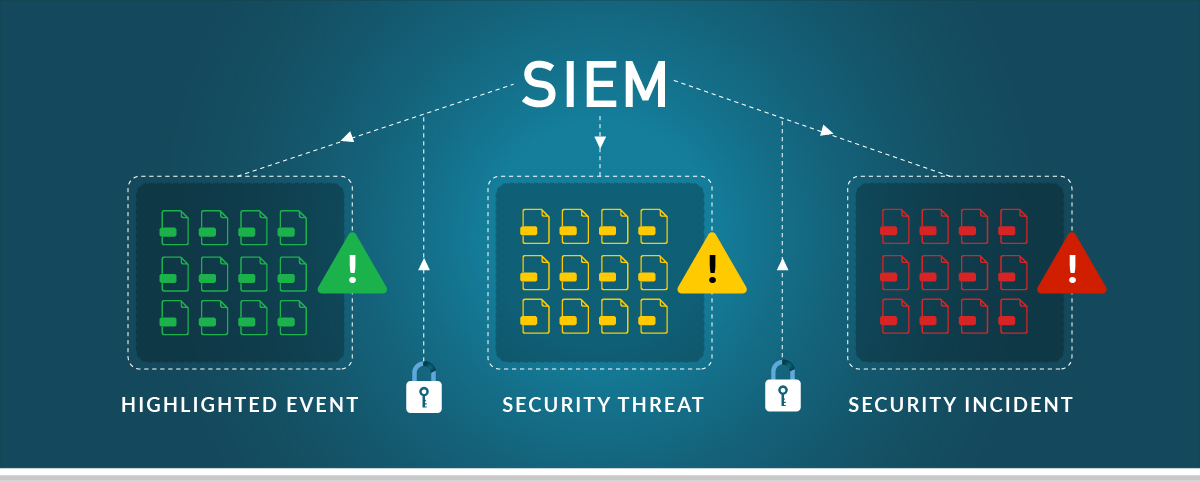
A SIEM provides built-in guidance for which events need to be dealt with immediately. However, all events can be classified in a variety of ways. A SIEM is highly configurable and can indicate how serious the event is to varying degrees of specificity. For example, it may be tied to a specific regulatory framework or placed into general categories of severity, such as:
- Highlighted Event – An event noted only for its irregularity. May or may not need further action depending on further analysis.
- Security Threat – A security threat is an event that may not be posing immediate risk but should be investigated as soon as possible.
- Security Incident – A security threat that indicates an imminent threat, or an attack that is taking place. Requires immediate action.
Escalation
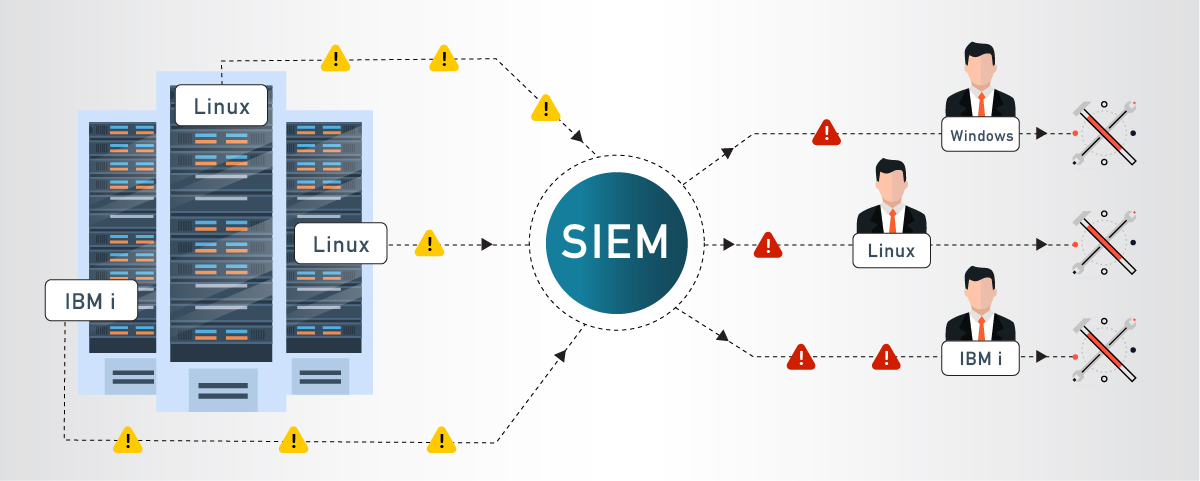
Without a SIEM
While a syslog server can send out alerts, they are typically sent for every event of a certain type (e.g. WARNING), to everyone. Response time is delayed as issues are parsed out and assigned to the appropriate team members.
With a SIEM
A SIEM will generate alerts and send out notifications to exactly the right security team members when a threat requires action. These real time alerts allow staff to act quickly to prevent or neutralize risks.
For example, if a SIEM sent out an alert that a virus has been detected on a Linux server, endangering sensitive data, an alert would be sent to the Linux admin who is best equipped to quarantine the server to prevent further infection until the virus is removed.
Alternately, a SIEM could launch an alert if someone was attempting to access a privileged account with multiple password guesses. A security admin or an automated response could lock out the account until additional verification was made, or security analysts made further investigations.
Analysis

Without a SIEM
While some analysis can be completed, the time spent working to interpret, assign, and handle the threat often leaves fewer resources for analysis. Security teams in these environments have to develop a mindset of putting out fires, with no time or personnel left to investigate the cause.
With a SIEM
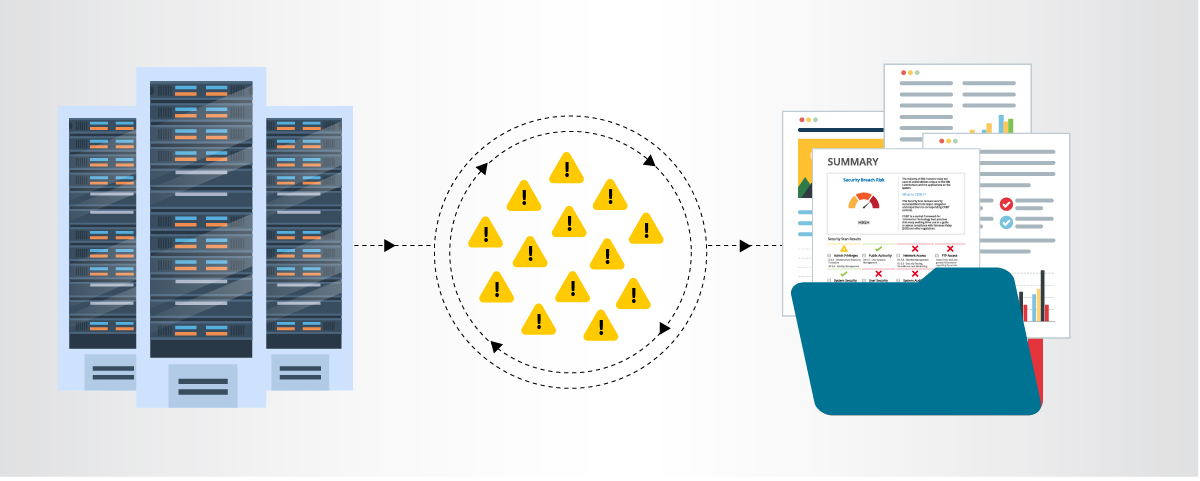
Security teams can use a SIEM to complete a thorough examination and analysis. As discussed above, raw data is stored from an event, and a SIEM can also generate reports with varying degrees of detail that document the lifecycle of an event. Security teams can annotate these reports with notes that record their investigation, as well as recommendations on actions to take for similar events. These reports become critical documentation that demonstrates an overall picture of an organization’s cybersecurity.
Compliance
Without a SIEM
Security teams often struggle to maintain compliance, since maintaining records and logs is a manual, and therefore much more tedious venture. As mentioned above, time and resources are scarce, and regulations may not be as heavily prioritized.
With a SIEM
Raw data flagged when a security event occurs is kept on record for a given period of time to maintain compliance for retention regulations. Reports generated by SIEMs create a complete audit trail, keeping an organization compliant with little effort.
While SIEMs provide a clear path to dealing with security threats, saving time is the biggest advantage that a SIEM solution provides. Security Teams are perpetually busy protecting their organization’s data, and time spent on tasks that could be automated is time wasted. Not only that, it is time that is often desperately needed to prevent or battle harmful threats that could cost an organization time, money, and even their reputation.
Ready to see Powertech Event Manager in action?
Watch a short demo to learn more about our SIEM solution and its features.

